This concludes our article series on DDoS protection in a connected world. This week we'll shift our focus from experiencing DDoS attacks to defending against them.
So far, we’ve covered the evolution of DDoS and how it impacts data centers and cloud ecosystems. Now, let’s dive into specific DDoS attacks and how to defend against them.
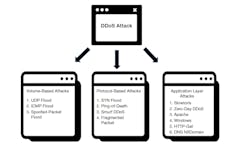
There are three types of DDoS attacks on which we will focus.
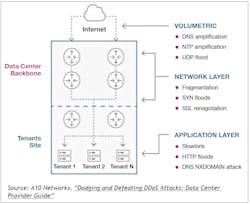
- Volume-Based Attacks. The strategy here is to flood networks with heavy volumes of data. Think of it as a pileup on a freeway. This massive amount of additional network traffic will consume bandwidth, shut down services, prevent users and customers from accessing essential services and sites, and bring a business down to a crawl. For data center providers, a massive DDoS attack could slow down several clients sharing bandwidth. There are various ways a volumetric attack can happen, including botnets, reflection, and amplification, and the attack often uses connectionless UDP as the delivery method. While this attack can be easy to detect, it can get very challenging to mitigate.
- Network Protocol Attacks. Network protocol layer attacks aim to exploit your network’s protocol weaknesses. You could be in trouble if you have poorly configured layer 3 and 4 policies. Simple attacks can include SYN floods or pings of death, and more sophisticated attacks go after higher-layer SSL handshake renegotiations.
- Application Layer Attacks. At the application layer, we use many services to allow the app to run. The Application layer attacks aim at application platforms, web servers and services, APIs, libraries, and even the application itself. These attacks are usually a lot more targeted and planned out in advance. Malicious actors will do their homework to understand the application, user interaction, app behavior, and potential weaknesses.
As a data center provider, you already have much to worry about. However, keeping your networks safe is a crucial business aspect you can’t ignore. Telecommunications and network management have come a long way. And our ability to lock down and segment networks has advanced as well. However, right alongside are the malicious actors advancing their tactics as well.
For data center providers, DDoS attacks are now more dangerous than ever. Malicious actors want the data that data centers store. So, what happens when a DDoS attack is just the tip of the spear?
Now that you have a solid framework on DDoS threats, it’s key to broaden our perspective on these attacks. Specifically, what happens when a DDoS attack is only a distraction?
DDoS as a Smokescreen
To begin, there will usually be a motive for an attack. In today’s connected world, a DDoS attack may be launched for more reasons than just taking down a website or a service. We mentioned smokescreens in a previous article. Usually, a malicious actor, sometimes a nation-state, will launch a DDoS attack to remove security resources and use the attack as a smokescreen to access other parts of the network. When DDoS is used as a smokescreen, these other activities may be happening:
- Infrastructure reconnaissance. While you’re fighting back a DDoS attack, malicious actors might be pocking at infrastructure and network pieces to understand your security posture better. They’ll look for vulnerabilities, out-of-date equipment, unpatched systems, and more.
- Malware deployment. While a DDoS attack is ongoing, malicious actors can take the time to deploy malware to user devices or parts of your infrastructure. The goal could be a bigger target where malware and DDoS are used to deprecate further a company’s threat detection, mitigation, and response capabilities.
- Data loss and exfiltration. Losing data is one of the most stress-inducing security events that could happen. Unfortunately, data exfiltration is the ultimate goal of a malicious actor. During a DDoS attack, malicious actors may leverage vulnerabilities or previously deployed malware to remove confidential data, PII, proprietary information, and customer data.
How Do You Detect Malicious Traffic?
There are two critical methods for detecting malicious traffic. DDoS attack traffic should be mitigated as close to the network edge as possible.
- Analyzing the metadata of traffic flow data — best for volumetric attacks
- Packet inspection — effective for all three types of attacks
To detect these attacks, consider the following:
- Volumetric Attacks. Remember, this attack focuses on flooding your network with traffic. A good edge router with a flow-based analysis strategy is an excellent way to detect these attacks quickly.
- Network Attacks. These attacks aim at your network’s weaknesses, and a good traffic monitoring system will allow you to spot anomalous traffic patterns. Usually, lopsided SYN to FIN packets is a good indicator of detecting a network layer attack.
- Application Layer Attacks. Attacks at the application layer are sophisticated and dangerous, and they will exploit the logic of your application or an application hosted by one of your tenants.
Outside of solid development practices, detection might require the analysis of a packet’s payload (GET vs. PUT) to detect if an attack is happening against an application or an app service.
Finally, there are two ways to deploy mitigation strategies.
- Proactive Approach: One of the best ways to ensure proactive mitigation is through in-path packet inspection. This will help detect and mitigate the three types of attacks we discussed. However, this becomes more challenging the larger you are. The larger the pipe, the more expensive it becomes to scan ingress and egress traffic. Usually, this kind of service is deployed to protect specific applications like DNS.
- Reactive Approach: While this method is excellent for detecting volumetric attacks, it’s not as great with network layer attacks and even less effective with application layer threats. Reactive DDoS mitigation involves analyzing out-of-band traffic metadata and flow data (NetFlow, sFlow, IPFIX) alongside on-demand mitigation. These flow-data deployments work well because they provide a full meta-data-level view of the network. You can then over-subscribe and apply demand to only one portion of the network under attack. This model is deployed to protect colocation services and provide DDoS scrubbing services.
What Should I Be Looking for in a DDoS Solution?
There’s never a silver bullet regarding the security of an entire infrastructure. However, there are vital considerations when selecting a solution for DDoS protection. Narrowing it down a bit, here are three critical considerations for data center providers when choosing a DDoS solution:
- Aim for precision. Working through false positives, negatives, or other detection errors is a huge time constraint. Also, you might miss something important. Without accuracy, you’re susceptible to missed attacks, legitimate users experiencing issues, and even service downtime. One way to improve precision is through machine learning and AI. These tools act as real-time DDoS weapons that help sharpen your solution and keep it on target.
- Can you scale? The amount of newly connected devices accessing the typical networks has grown on a massive scale. Within the data center, we see the convergence of IT (information technology) and OT (operational technology) as more devices within critical infrastructure come online. With so many IoT and connected devices, it’s sometimes hard to have a DDoS solution that can scale alongside your requirements. Be sure your DDoS solution can grow as quickly as your connections.
- Efficiency during an emergency. Suppose you’re under attack, every single second counts. You will need a solution that can be as automated as possible. In cases of an emergency, you want to have as few manual processes as possible. Look for policy-driven DDoS solutions with automated escalation capabilities, detecting attack patterns and leveraging machine learning to improve mitigation effectiveness.
If you’re a data center, service provider, or an organization that’s rapidly scaling out, there are two additional points to consider:
- Intelligent automation. Look for detection and mitigation capabilities. The critical difference is that these need to be automated to relieve scarce security resources of routine tasks. Intelligent automation will also enable quick identification of more sophisticated and constantly evolving attacks and enable auto-learning and reporting.
- Subscriber and service provider visibility. For data center and colocation service providers to create in-depth DDoS visibility, you will need a tool that quickly sees service impacts to infrastructure and enable tenant/subscriber visibility. For those offering DDoS protection as a value-added service, providing a portal that the tenant/subscriber can access will increase your value to that tenant.
Download the entire special report, The Security Gap: DDoS Protection in a Connected World, featuring A10, for an exclusive real-world data center provider use case where modern DDoS solutions impact network protection and creates a business opportunity.
About the Author